Tech News
7 Extinction-Level Cybersecurity Threats
The dinosaurs never saw their end coming. The same is true for businesses that don’t understand what an extinction-level cyberthreat can do to their business an
30 October, 2025The Anatomy of a Cyber-Ready Business
Cyberattacks are no longer rare events. Every business, from startups to established companies, faces digital risks that can disrupt operations and compromise c
30 October, 2025Windows 10 End of Life Looms: Is Your Business Ready
Understanding Windows 10 End of Life and Its Implications As technology relentlessly advances, the inevitability of obsolescence looms large. For Windows 10, th
17 September, 2025How investing in technology increases revenue and efficiency for YOUR business
Introduction to the Importance of Technology Investment in Business In today’s fast-paced and ever-evolving business landscape, technology is not just an
08 September, 2025Email SaaS Protection: Safeguarding Your Small Business
In an era dominated by digital transformation, small businesses are increasingly reliant on cloud-based services for their day-to-day operations. Among the myri
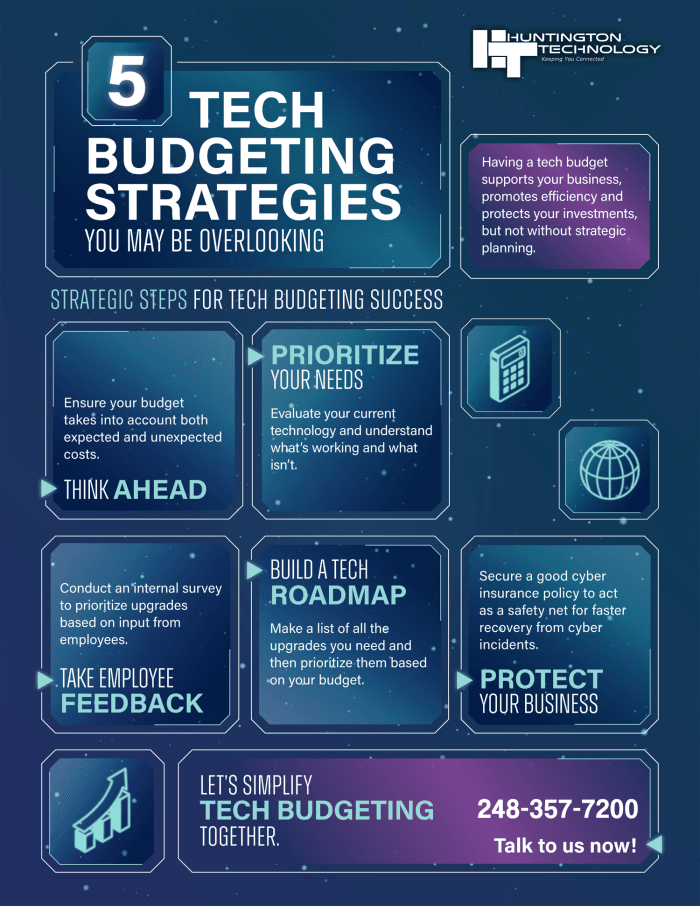
24 April, 20255 Tech Budgeting Strategies
As you prepare your budget for the upcoming year, it’s crucial to recognize that technology investments are key drivers of success, not just operating costs. Bu
14 November, 2024NIST Disaster Recovery Plan Template
Cybersecurity is a major concern for every company today, as data is becoming exponentially more important in nearly every aspect of business. With increased us
13 June, 2024How to Create a HIPAA Disaster Recovery Plan
Having a disaster recovery plan is essential for any business, as it results in better recovery of data when an unexpected event such as a weather incident or c
06 June, 2024Business Continuity vs Disaster Recovery: A Guide to Key Differences
Businesses that are concerned with what would happen if a disaster struck are often focused on what’s known as a disaster recovery plan. This plan takes a well-
30 May, 2024Disaster Recovery Site Requirements
When disaster strikes, can your business still remain operational? If you don’t have a disaster recovery plan in place, and a disaster recovery site to relocate
23 May, 2024Passwords They seem to have been with us forever
As we continue to suggest things you can do to protect the integrity of your company and customer data, here is a blog that covers an old level of security that
20 December, 2023Prying eyes: Keeping your data safe
Even the simplest business possesses data that is proprietary and confidential. Customer and prospects lists, sales data, and personal data about customers such
13 December, 2023Four Basics to follow for Everyday Data Security
One of the biggest questions we get from clients and prospects is “What can we do to protect ourselves from cyber attacks?” It is a sensible concern. A cy
06 December, 20235 ways to make passwords more effective
You should be using an array of security tools to protect your business data. Some can be highly sophisticated, but there is one tool that we all still rely on
29 November, 2023Why Migrate to the Cloud
If you haven’t already considered migrating your data storage to the cloud, you are probably in the minority of businesses. While it may seem intuitive th
22 November, 2023Protecting Your Data on the Cloud
Cloud storage has transformed the way businesses store and manage data, but for some, it also raises concerns about data protection. This blog post discusses a
15 November, 2023Your Cloud Questions: Answered
Your Cloud Questions: Answered The cloud is now the preferred method for data storage. However, justified or not, there are a few worries you might have about m
08 November, 2023Cloud storage can save you money?
In this blog post, we will explore how cloud storage can support your firm. For SMBs, data loss or system failures can be catastrophic, leading to significant f
01 November, 2023Your employee quit your organization Make sure your data hasn’t
Your employee quit your organization. Make sure your data hasn’t When someone new joins your organization, how do you manage their onboarding? Chances are, you
18 October, 2023System and software updates: Why you shouldn’t be skipping them for later
System & software updates: Why you shouldn’t be skipping them for later We all know how annoying it can be when you get a pop-up asking if you’d like to upd
04 October, 2023A “Free” Covid Vaccine can give you a virus (and infect your IT network)
A “Free” Covid Vaccine can give you a virus (and infect your IT network) With the pandemic still raging in most parts of the world, cybercriminals have come up
27 September, 2023What does cyber insurance typically cover?
What does cyber insurance typically cover? Pandemic or no pandemic–cyber insurance is a must-have. And, not just that, some of your clients may insist tha
13 September, 2023Why does your business need cyber insurance?
Why does your business need cyber insurance? The WFH model makes businesses much more vulnerable and easy targets for cybercriminals. Some of the reasons includ
06 September, 2023Data security in a WFH setup
Do you have staff working from home? With the pandemic still around, the answer to that question is most likely a “Yes”. And, that makes sense too, why risk the
23 August, 2023The challenges in establishing data security best practices
The challenges in establishing data security best practices in a WFH environment The COVID-19 pandemic changed the landscape of the corporate world drastically
16 August, 2023Demystifying Ransomware: Understanding its Impact on Businesses
Demystifying Ransomware: Understanding its Impact on Businesses In today’s interconnected digital landscape, cyber threats continue to evolve and pose sig
02 August, 2023What an MSP do that you can’t to protect yourself from Ransomware
Managed Service Providers are experts in protecting against cybercrime, just as you are an expert in producing and selling a product or service. Focus your ener
26 July, 2023Protecting Your Business: Safeguarding Against Ransomware Attacks
In today’s digital age, businesses face an ever-increasing threat from cybercriminals, and one of the most prevalent and damaging forms of cyberattack is
19 July, 2023Leave virus protection to your MSP Doctor
Leave virus protection to your MSP Doctor Cyberattacks on individuals and businesses for nasty purposes is nothing new. Stealing data, disrupting business, nati
28 June, 2023Passwords: boring but they matter
Passwords: boring but they matter Passwords are something that you and every employee can use to protect your data and maintaining this important protective wal
21 June, 2023Four easy ways to thwart cyber criminals
Four easy ways to thwart cyber criminals With all the talk about cybercrime and the recent spate of headlines about ransomware, concerns for your data security
14 June, 2023Three common sense data safety reminders
Three common sense data safety reminders When it comes to smaller and medium sized businesses, anything that distracts from the day to day concerns about bringi
31 May, 20237 Cybersecurity basics to never forget
No matter how much people hear “data safety,” they still can get sloppy about their cybersecurity. One of the reasons is that there are so many constant reminde
24 May, 2023Password Hygiene Best Practices
Password Hygiene Best Practices According to a report by Verizon, 80% of data breaches are caused by weak or stolen passwords. In addition, the report found tha
17 May, 2023Password Management Tools: An overview
Effective password management is an essential aspect of cybersecurity. With the increasing number of online accounts and services, remembering all those passwor
10 May, 2023Fix that lock…and get a spare key! Software updates, security patches and data backups
If the lock to your home’s main door breaks, do you fix it or just let it be? My guess is, you would get a locksmith to fix it for you at the earliest. And, wha
26 April, 20235 Ways SMBs Can Save Money on Security
5 Ways SMBs Can Save Money on Security Small-to-medium sized businesses and large enterprises may seem worlds apart, but they face many of the same cyber-secu
19 April, 2023Don’t leave yourself unprotected
Phishing email statistics suggest that nearly 1.2% of all emails sent are malicious, which in numbers translated to 3.4 billion phishing emails daily. Extortion
12 April, 2023Four Key Components of a Robust Security Plan Every SMB Must Know
Four Key Components of a Robust Security Plan Every SMB Must Know Most businesses are now technology dependent. This means security concerns aren’t just worri
12 April, 2023Just Because You’re Not a Big Target, Doesn’t Mean You’re Safe
Just Because You’re Not a Big Target, Doesn’t Mean You’re Safe Not too long ago, the New York Times’ website experienced a well-public
05 April, 2023Stay Secure My Friend More Hackers Targeting SMBs
Stay Secure My Friend… More Hackers Targeting SMBs Many SMBs don’t realize it, but the path to some grand cybercrime score of a lifetime may go right th
29 March, 2023Cloud Monitoring Can Be the Difference Maker for SMBs
Cloud Monitoring Can Be the Difference Maker for SMBs It’s a fast-paced world. Not only do people want things, they want things right now. This sometimes-unne
22 March, 2023Why Hybrid Clouds are More Than Just Another Trend
Why Hybrid Clouds are More Than Just Another Trend It should come as no surprise that many small to midsize business owners take pride in overseeing every asp
15 March, 2023Why More SMBs are Turning to the Cloud to Reduce TCO
Why More SMBs are Turning to the Cloud to Reduce TCO More small and mid-size businesses (SMBs) seem to be taking the initiative to learn more about the benefi
08 March, 2023How SMBs Can Utilize the Cloud To Build Their Business
How SMBs Can Utilize the Cloud To Build Their Business There has been a lot of talk lately about the cloud and its ability to put small to midsize businesses
01 March, 2023Why SMBs Must Proactively Address the Threat of Mobile Hacks
Why SMBs Must Proactively Address the Threat of Mobile Hacks More cyber criminals are targeting small-to-medium sized businesses. One reason for this is too m
15 February, 20233 Things to Consider Before Jumping Into BYOD
3 Things to Consider Before Jumping Into BYOD You’ve read it time and time again. “Bring Your Own Device” isn’t a trend, it’s the future. Workplaces where com
08 February, 2023A Smarter Approach to Mobile Device Management
A Smarter Approach to Mobile Device Management More people today use personal mobile devices like smartphones and tablets for business purposes. Such devices,
01 February, 2023- 30 January, 2023
4 Essential Pieces to Any Small Business BYOD Strategy
4 Essential Pieces of Any Small Business BYOD Strategy Believe it or not, once upon a time, kids at the bus stop didn’t have cell phones and the mobile device
25 January, 2023Keep Your IT Guy and Outsource IT Services, Too
Keep Your IT Guy and Outsource IT Services, Too Everyone in the office loves Eric. Sporting a different ironic t-shirt everyday, Eric is the one we call when
18 January, 2023How to Trim the Fat From Data Center Costs
How to Trim the Fat From Data Center Costs When smaller businesses look to cut costs, they commonly take shortcuts that are risky to their bottom line. They may
11 January, 2023Click, Click, BOOM – You’re in Business But Is Your Technology Ready?
Click, Click, BOOM – You’re in Business But Is Your Technology Ready? It’s a fast business world. Brilliant business ideas can be conjured up at som
04 January, 2023Three Steps To Fix IT Management for SMBs
Three Steps To Fix IT Management for SMBs Small-to-medium-sized businesses (SMBs) tend to have a more difficult time managing IT than larger enterprises. Desp
28 December, 2022Inquiring SMBs Want to Know What’s the Difference Between a Help Desk and NOC?
Inquiring SMBs Want to Know… What’s the Difference Between a Help Desk and NOC? It’s no secret that any growing small-to-medium sized busine
21 December, 2022Understanding Managed Services and How They Benefit SMBs
Understanding Managed Services and How They Benefit SMBs Small to medium sized businesses (SMBs) receive a lot of calls each day from slick sales people peddl
14 December, 2022Are Managed IT Services Right For You? A Few Things to Consider
Are Managed IT Services Right For You? A Few Things to Consider How do you get a small business to recognize the value of manages IT services? In the start-up
07 December, 2022Is That A Business Continuity Plan in Your Pocket Or A Bunch of Jargon?
Is That a Business Continuity Plan in Your Pocket or a Bunch of Jargon? Technology is full of difficult jargon. To further complicate things, certain terms ar
23 November, 20228 Cold Hard Truths for SMBs not Worried About Data Recovery and Business Continuity
8 Cold Hard Truths for SMBs Not Worried About Disaster Recovery and Business Continuity The foundation of any successful business continuity solution is the abi
16 November, 2022Six Steps to Better Data Backup and Quicker Recovery
Think Quicker Recovery Time, Not Quicker Backup – While incremental backups are much faster than executing a full-backup, they also prolong recovery tim
12 October, 2022Seven ‘Must Haves’ for Your Small Business Website
Your website represents your business and so building and maintaining it need to be of primary concern to you as a business owner. We often find business ow
04 October, 2022Is your Business Safe from Virtual Threats?
Did you know that 50% of small business owners think their businesses are too small to be targeted by the thieves of the virtual world? Contrary to popular
20 September, 2022How Much Does Downtime Really Cost Your Business?
Many SMB owners think IT downtime only costs them a few productive hours, but there’s a lot more at stake when your systems go down. Customer satisfaction and l
06 September, 2022Has Your Website Been Optimized for Mobile Users?
Did you know that this year there will be more mobile web surfers than stationary ones? That means more prospects are accessing your business website more t
30 August, 2022Seven things that pandemic taught us about data security
Seven things that pandemic taught us about data security As workers fled home to handle everything remotely, organizations had to quickly address new threats an
15 March, 2022Stars of the show: Cloud and VOIP
Stars of the show: Cloud and VOIP Despite annoying challenges presented by the abrupt shift to the WFH model thanks to the pandemic, there were some tech heroes
08 March, 2022Two reasons to pay attention to software
Two reasons to pay attention to software Software matters. What your employees use can impact your firm and your customers. Pay attention. Make rules. New softw
01 March, 2022Access matters when things go to **and?)!
Access matters when things go to **&?)! The COVID-19 pandemic brought a multitude of lessons along with it, on both the personal and professional fronts. Fr
22 February, 2022Outsourcing: an overview
Outsourcing: an overview Outsourcing today simply involves using external entities to handle specific, specialized business functions so that organizations can
15 February, 2022Can you do this at home?
Can you do this at home? Outsourcing HR, real estate portfolio management, tax audits, etc is fairly common nowadays. This whitepaper discusses another function
08 February, 2022MSPs save money And you get stuff that matters
Outsourcing has become a fairly common element in business processes today. What started off as a means to cut business costs and take advantage of cheaper reso
01 February, 2022Quality matters: Get the best
Quality matters: Get the best IT is one of the core functions of any business. There’s no aspect of a business that is untouched by IT. Outsourcing IT is a big
25 January, 2022Train your staff: Your first and best firewall
Train your staff: Your first and best firewall Protecting your organization against cyber threats can seem like a challenge that involves extremely high-tech wi
18 January, 2022Three best practices to protect your data
Three best practices to protect your data. While malware and phishing attacks have evolved over time and are constantly becoming more and more sophisticated, th
11 January, 2022Ransomware vs other malware attacks
Ransomware vs. other malware attacks There is no end to the volume and type of malware out there in cyberspace. For a very long time, organizations were aware t
04 January, 2022Everyone wants to go phishing
Everyone wants to go phishing. You are very much aware that your company or organization is at risk, every minute of the day, from cyberattacks, malware, ransom
28 December, 2021You’ve been hijacked!
You’ve been hijacked! Has it ever happened to you that you opened the web browser on your PC and it looked a bit off? Then you perhaps did a Google search for s
22 December, 2021Your employee quit your organization Make sure your data hasn’t
When someone new joins your organization, how do you manage their onboarding? Chances are, you already have processes in place for everything. The employee pape
15 December, 2021VPN 101: Remote access and safety
VPN 101: Remote access and safety As we know, the Coronavirus pandemic has brought about a paradigm shift in the way businesses function. Home is now, ‘The Offi
08 December, 2021System and software updates: Why you shouldn’t be skipping them for later
System & software updates: Why you shouldn’t be skipping them for later We all know how annoying it can be when you get a pop-up asking if you’d like to upd
01 December, 2021A “Free” Covid Vaccine can give you a virus (and infect your IT network)
A “Free” Covid Vaccine can give you a virus (and infect your IT network) With the pandemic still raging in most parts of the world, cybercriminals have come up
24 November, 2021Cyber Security training basics: Password best practices
Cyber Security training basics: Password best practices & phishing identification As a business you know the importance of ensuring that your data is safe f
17 November, 2021What does cyber insurance typically cover?
What does cyber insurance typically cover? Pandemic or no pandemic–cyber insurance is a must-have. And, not just that, some of your clients may insist tha
10 November, 2021Why does your business need cyber insurance?
Why does your business need cyber insurance? The WFH model makes businesses much more vulnerable and easy targets for cybercriminals. Some of the reasons includ
03 November, 2021WFH means more vulnerability to cybercrime
WFH means more vulnerability to cybercrime. Here are some methods to stay safe WFH opens up whole new horizons in terms of flexibility, productivity, and cost s
27 October, 2021Data security in a WFH setup
Data security in a WFH setup Do you have staff working from home? With the pandemic still around, the answer to that question is most likely a “Yes”. And, that
20 October, 2021The challenges in establishing data security best practices
The challenges in establishing data security best practices in a WFH environment The COVID-19 pandemic changed the landscape of the corporate world drastically
13 October, 20214 Lesser-known benefits of hiring an MSP
4 Lesser-known benefits of hiring an MSP You are probably aware of the most common benefits of signing up with an MSP such as On-demand IT support: Having an MS
30 June, 2021Know your IT risks
Whether you have your in-house IT team, or have outsourced your IT needs to be taken care of by a Managed Services Provider, you need to know what are the possi
25 June, 2021What to consider when investing in cyber insurance
What to consider when investing in cyber insurance As a business, you are probably aware of the term, cyber insurance. With the cybercrime rates rising consiste
24 June, 2021Cyber insurance: What’s the cost and what does it cover
Cyber insurance: What’s the cost and what does it cover Cyber insurance covers a range of elements, the most basic being the legal expenses incurred as a result
23 June, 2021Cyber insurance 101
Cyber insurance 101 What is cyber insurance With cybercrime becoming a major threat to businesses across the world, irrespective of their size, cyber insurance
22 June, 2021How the Coronavirus crisis is the gateway to the other kind of virus
How the Coronavirus crisis is the gateway to the other kind of virus To say the COVID-19 pandemic gave the whole world a tough time would be an understatement.
15 June, 2021Your employee’ social media account was hacked How does it affect you?
Your employee’ social media account was hacked. How does it affect you? Did you know that social media accounts are one of the favorite targets for cybercrimina
08 June, 2021Are your data security measures strong enough?
Are your data security measures strong enough? Let me start this blog by asking you a question. How did your business respond to the security threats brought on
01 June, 2021WFH is here to stay Are you ready?
WFH is here to stay. Are you ready? The year 2020 was nothing like what we had seen before. At a certain point in time, it felt like the world would come to a s
25 May, 2021Data security in the ‘Work-from-home’ environment
Data security in the ‘Work-from-home’ environment 2020 threw a lot of challenges at the world. One of them, from the business perspective, that overshadowed the
18 May, 2021How the cloud is a solid survival tool for your business during a crisis
How the cloud is a solid survival tool for your business during a crisis One thing the Coronavirus pandemic taught businesses is the fact that it is important t
17 May, 2021Tech agility: A must-have for crisis survival
Tech agility: A must-have for crisis survival It is a known fact that survival of any species depends on its ability to adapt to change. One major change for bu
16 May, 2021What the COVID-19 crisis taught us about the cloud and business continuity
What the COVID-19 crisis taught us about the cloud and business continuity The COVID-19 pandemic has changed life as we know it, in many ways. While its impact
15 May, 2021What’s your argument against an SLA with an MSP? Part-2
What’s your argument against an SLA with an MSP? (And why it doesn’t hold water) Part-2 In our last blog post, we discussed 3 reasons SMBs usually cite for not
14 May, 2021What’s your argument against an SLA with an MSP? Part-1
What’s your argument against an SLA with an MSP? (And why it doesn’t hold water) Part-1 Managed IT services are becoming more popular by the day. Businesses, bi
13 May, 2021Equip your business with the IT foundation it needs to compete and win
Equip your business with the IT foundation it needs to compete and win In a recent industry survey, it was found that one of the biggest factors holding back sm
12 May, 2021Transitioning from average to best-in-class with IT
Transitioning from average to best-in-class with IT Many small or mid-sized businesses don’t focus much on IT as they should. For a lot of them, the focus is on
10 May, 2021WFH: Remote Data Access and Data Security
WFH: Remote Data Access and Data Security This may be the single biggest concern you may have to address when looking at WFH. When your employees are working in
02 February, 2021Three different issues about WFH you may have not considered.
Three different issues about WFH you may have not considered. Today’s blog is a look at three different issues that don’t get much coverage in discussions of th
26 January, 2021WFH: How we got here.
WFH: How we got here. If you’ve been in the workforce for a while, you remember what life in the office was like a few decades ago. The uniformity of the struct
19 January, 2021The Positives of WFH
The Positives of WFH You are probably caught up in overseeing a Work-From-Home policy that you may have never intended to initiate. It can be concerning, and th
12 January, 2021Keylogger 101
Keylogger 101 We have all heard of hacking, virus, ransomwares, etc. as they keep coming up in the news every now and then. But, have you heard of keyloggers? I
07 January, 2021Understand your Cookie to manage it better!
Understand your Cookie to manage it better! There are 3 kinds of cookies, each having different functions. One of them is session cookies. If it weren’t for ses
05 January, 2021Social media security
Social media security Social media is a great tool for SMBs to get the word out about their products and services, and also to build their brand and connect wit
31 December, 2020How to manage cookies effectively so they are not a threat to your data
How to manage cookies effectively so they are not a threat to your data Avoid third-party cookies: Third-party cookies are primarily used for online advertising
29 December, 2020Five reasons to invest in a password management system ASAP
Five reasons to invest in a password management system ASAP Password management tools are software programs that put up enough security and safety mechanisms in
24 December, 2020Gaining a competitive edge during the pandemic
Gaining a competitive edge during the pandemic The COVID-19 pandemic has been tough on everyone. The lockdowns, the need to follow social distancing–thoug
22 December, 2020Insider threats: Not as uncommon as you think
Insider threats: Not as uncommon as you think When we speak of cybercrime and data theft, we typically think of seasoned cybercriminals. But you’d be surprised
17 December, 2020Eight common password mistakes to avoid
Eight common password mistakes to avoid Research points out that more 80% of data breaches happen due to password hacking, meaning that poor password hygiene is
15 December, 2020Best practices for remote desktop access
Best practices for remote desktop access Remote desktop access is an essential in these days when businesses are expected to be responsive to their clients almo
10 December, 2020Three things to consider when investing in new software
Three things to consider when investing in new software When running a business, you will often find yourself in need of new software tools to enhance the produ
08 December, 2020Everyone loves cookies–even cybercriminals
When you visit a site, probably for the first time or from a new device or browser, you will see an alert that mentions the site uses Cookies to offer you a mor
03 December, 2020Social media at work what could go wrong?
As a business, there is no doubt today that you need to make your presence felt on major social media platforms such as Facebook, Twitter, Instagram and LinkedI
24 November, 2020Four reasons to opt for the co-managed IT services model
Four reasons to opt for the co-managed IT services model Co-managed IT services model is one in which the business has its own IT team, but still contracts with
19 November, 2020Why MSP relationships fail
Why MSP relationships fail A lot of SMBs opt for managed service providers who can help handle their IT requirements, and for the most part, it works well. Almo
17 November, 2020Best practices for data safety in a remote work environment
Best practices for data safety in a remote work environment Do you have staff working from home? Of late, due to the Coronavirus crisis a lot of businesses shif
12 November, 2020Do your homework: 3 things to do when looking for an MSP
Thinking of hiring a Managed Service Provider, but not sure how to go about it? Here are a few things to do before you zero in on one. Figure out what you have
10 November, 2020Multi-Factor Authentication 101
Multi-Factor Authentication 101 You have probably already come across the term multi-factor authentication. The concept is not new, but has caught on really qui
05 November, 20205 Lesser known benefits of choosing the co-managed IT model
5 Lesser known benefits of choosing the co-managed IT model Even companies with IT staff on their payroll can’t deny having an MSP onboard offers benefits that
03 November, 20204 things to do to ensure your business continuity planning is a success
4 things to do to ensure your business continuity planning is a success Working on creating a contingency plan for your business? That’s great! Here are 4 thing
29 October, 2020How safe is your data when your staff works from home?
How safe is your data when your staff works from home? The Coronavirus crisis has changed the world as we know it. With social distancing, lockdowns and work fr
22 October, 2020What are the essentials of a business continuity plan?
What are the essentials of a business continuity plan? An unexpected emergency can wipe out your business! A business continuity plan can help it survive. But,
15 October, 20203 Reasons to prepare a business continuity plan
3 Reasons to prepare a business continuity plan if you haven’t done so already A business continuity plan is the blueprint you need during an emergency to keep
08 October, 2020Business continuity planning: A must-have, not a luxury
Business continuity planning: A must-have, not a luxury Business continuity planning is not an alien concept anymore. In recent times we have witnessed a lot of
01 October, 2020Mitigate Costly New Technology Risks for Continued Stability and Profitability
Partnering with a managed service provider (MSP) is one new approach being used by many companies like yours. Experienced MSPs have access to newer tools that r
24 September, 2020Is your Business Safe from Virtual Threats?
Did you know that 50% of small business owners think their businesses are too small to be targeted by the thieves of the virtual world? Contrary to popular
17 September, 2020Is That Email a Phishing Scheme?
Research has revealed that over half of all users end up opening fraudulent emails and often even fall for them. Phishing is done with the aim of gathering
10 September, 2020How Much Does Downtime Really Cost Your Business?
Many SMB owners think IT downtime only costs them a few productive hours, but there’s a lot more at stake when your systems go down. Customer satisfaction and l
03 September, 2020Has Your Website Been Optimized for Mobile Users?
Did you know that this year there will be more mobile web surfers than stationary ones? That means more prospects are accessing your business website more t
27 August, 2020Five Ways Your Business Can Improve Its Search Engine Rankings
In an age where most business happens online, not showing up in Google search results can really hurt you. While there’s no real shortcut to showing up consiste
20 August, 2020Five Things You Should Do Right Now to Preserve Your Network and Systems
1. Backup Files Every Day – As catastrophic as data loss is, the number of businesses that still are not backing up their network is unbelievable. Accordi
13 August, 20204 things to consider before starting a WFH initiative
4 things to consider before starting a WFH initiative In our last blog, we talked about 5 things to plan and analyze before you initiate a WFH policy. In this b
30 July, 2020Implementing work from Home: Planning Matters
Implementing work from Home: Planning Matters Work From Home, also commonly known as telecommuting, is a fairly general term that encompasses a range of workpla
23 July, 2020Why we still worry about Work from Home policies
Why we still worry about Work from Home policies If you have been in the workplace for a few decades, you may remember that the idea of telecommuting began to a
16 July, 20207 ways a Work From Home policy can help your business
7 ways a Work From Home policy can help your business In the last several years, the concept of WFH has become increasingly more popular. Though some still rema
09 July, 2020Cyber hygiene: The key to your business’s good cyber health
Cyber hygiene: The key to your business’s good cyber health We all know that basic hygiene is a must to lead a healthy life. Did you know that the same rule app
03 July, 2020Free Internet Access? Don’t fall for this one
Free Internet Access? Don’t fall for this one One of the popular internet scams that has been doing the rounds since 2017 is the one about “Free Internet”. This
26 June, 2020Online shopping? Watch out for these red flags
Online shopping? Watch out for these red flags Who doesn’t like online shopping? Online shopping has opened up a whole new world to us. Get whatever you want, w
19 June, 2020DNS Cache poisoning: What every SMB must know
DNS Cache poisoning: What every SMB must know In one of the most common poisoning attacks, the attacker poisons the DNS Cache with the aim of leading visitors t
12 June, 2020Huntington Technology’s On-site Visit Covid-19 Guidelines
Here at Huntington Technology, we are all working to keep everyone safe while assisting you with your technology. Below are some basic guidelines that we are ha
11 June, 2020Protecting yourself against poison attacks
Protecting yourself against poison attacks Data poisoning by way of logic corruption, data manipulation and data injection happen when the attacker finds a way
05 June, 2020Poison Attacks: A quick overview
Poison Attacks: A quick overview Smart technology is everywhere. Not just in our offices, but even in our day-to-day lives with tools like Google Home and Alexa
29 May, 2020Employee training and Cybersecurity
Employee training will form a big part of the cybersecurity initiative that you will take on as an organization. You need to train your employees to identify an
22 May, 2020Strengthening your cybersecurity policies
Strengthening your cybersecurity policies Formulating strong IT policies and laying down the best practices for your staff to follow is one of the best ways to
15 May, 2020StartupNation Radio Exclusive: How Small Businesses Can Survive COVID-19
Our very own Steve Krasnick, founder and CEO of Huntington Technology, provides tips on remaining productive (and safe) when working from home along with a slew
14 May, 2020Why do you need a top-down approach to IT security?
For any organization, its employees are its biggest assets. But, what happens when your biggest assets turn out to be your greatest threats or liabilities? That
08 May, 2020Security tips for working from home (WFH)
Huntington Technology wants to make sure with our current climate that everyone is staying safe not only physically, but virtually as well. Below are some great
06 May, 20203 steps you can take to protect your data in the Cloud
3 steps you can take to protect your data in the Cloud Moving to the Cloud offers tremendous benefits for SMBs that range from lower IT costs to any-time access
01 May, 2020Is the Cloud really risk-free?
Is the Cloud really risk-free? The Cloud presents plenty of benefits that make it a very attractive choice, especially for SMBs who don’t want to be burdened wi
24 April, 2020Things to consider before switching to the Cloud
Things to consider before switching to the Cloud More and more businesses are switching to the Cloud to store their data and rightly so. The Cloud offers numero
17 April, 2020Get smart about smartphones
Get smart about smartphones With flexible working schedules, remote teams and Bring Your Own Device (BYOD) policies in force, it is has become commonplace for e
06 December, 2019Why you need the cloud?
Why you need the cloud? When talking to our clients, we have noticed that SMBs often think the cloud is something for their bigger counterparts to explore. We h
29 November, 2019Don’t sign up with that MSP just yet!
Don’t sign up with that MSP just yet! The decision to sign up with a MSP is a big one–you are essentially trusting someone with the backbone of your busin
22 November, 2019The biggest threat to your IT infrastructure: Your own employees
The biggest threat to your I.T infrastructure: Your own employees Did you know that your employees often unwittingly ‘help’ cybercriminals gain access to your s
15 November, 20193 things your Managed Services Provider (MSP) wants you know
3 things your Managed Services Provider (MSP) wants you know Are you considering bringing a MSP on board? Or perhaps you already have one. Either way, for you t
08 November, 2019Don’t make these IT mistakes as you grow!
Don’t make these IT mistakes as you grow! During the course of IT consultancy, we come across a lot of clients who are not happy with the way their IT shaped up
01 November, 2019Hiring seasonal staff? Here are a few things to consider from the IT
Hiring seasonal staff? Here are a few things to consider from the IT perspective In many industries, there are seasonal spikes in business around specific times
11 October, 20193 Things to consider before you sign-up with a cloud services provider
3 Things to consider before you sign-up with a cloud services provider More and more SMBs are migrating to the cloud and that is not a surprise considering the
04 October, 2019Ransomware emails: How to identify
Ransomware emails: How to identify and steer clear of them Ransomware attacks have suddenly become more prevalent. Each year sees more of them. Hospitals, NPOs,
20 September, 2019How good is your password
How good is your password? Did you know that having a weak password is one of the biggest security risks you face? This blog focuses on the best practices relat
19 September, 2019Think you are too small
Think you are too small to be targeted by a cybercriminal? Think again. When I meet with clients, especially SMBs, I often hear them say that they feel t
18 September, 2019Keeping your data safe: Access Control
Keeping your data safe: Access Control Cyberattacks are a commonplace today. Malwares such as viruses, worms and more recently ransomwares not only corrupt your
17 September, 2019Cyberattacks and the vulnerability of the small business
Cyberattacks and the vulnerability of the small business You cannot go a day without reading about some big name company or even government agency being hacked
04 August, 2019Humans cause so much trouble
Have you been focusing on software packages and anti-virus tools to protect your data from hacking? That may not be enough, because it overlooks one of the bigg
22 June, 2019The most boring topic Ever
Yes, today’s blog is about office phone systems. You have one. They are dull, necessary, and no one wants to deal with them. They need to be re-configured for n
15 June, 2019The Cloud: what do you get?
The cloud refers to using off site computing resources and storage to supplement or even replace the use of on-site/in-house resources. Instead of buying hardwa
08 June, 2019What the cloud means for you–Part II
Recently, we talked about ways the cloud brings value, business protection, and economies of scale to the smaller firm that they could never achieve by themselv
01 June, 2019The Cloud means no more stormy weather
Many small firms are pretty busy handling their own business, and don’t give much thought to what they would do if a natural disaster from a bad snowstorm to mu
25 May, 2019Your front door is talking
If you’ve been following the news, the Internet of Things is getting increasing attention. You’re probably also thinking this is some Silicon Valley fancy
18 May, 2019Security and your sub-contractors
So you feel relatively comfortable that you have created cyber security around your data and your employees are trained to avoid security errors in their day-to
11 May, 2019Government regulations
Any business that stores customer payment information must comply with a number of state and federal regulations. The legal, healthcare, and financial sector
04 May, 2019NPO’s and volunteer security nightmare
Not-for-profits have an unusual issue regarding security. Firms that have trained, paid full-time employees have a strong level of control over the actions of t
27 April, 2019Cyber Crime and Security for SMBs
Did you know the illicit trading of personal data was worth $3.88 billion last year? Cybercrime is a growing industry known for its innovation. It goes far beyo
20 April, 2019Higher goals get dragged down by Tech: The NPO story
If you are a smaller Not-for-Profit, it is likely that your organization has been driven from its inception by individuals strongly motivated with a passion for
18 April, 2019Password basics people still ignore
You can have all the locks on your data center and have all the network security available, but nothing will keep your data safe if your employees are careless
16 April, 2019How the cloud saves smaller firms money
How the cloud saves smaller firms money OK. You pay someone to store all of your data in the cloud, as opposed to keeping it on your own server and backing it u
01 March, 2019Data regulation and our business: You are probably regulated these laws
Data regulation and our business: You are probably regulated these laws Small firms are probably aware that there are laws regulating the handling of data, but
22 February, 2019A security hack doesn’t have to mean the end of your company
A security hack doesn’t have to mean theend of your company Statistics are showing that each year over 50% of small firms are victims of a cyber attack or data
15 February, 2019Don’t steal… It isn’t nice and makes you vulnerable to security hacks
Don’t steal… It isn’t nice and makes youvulnerable to security hacks Don’t steal. It isn’t nice. And… it make you extremely vulnerable you security hacks
08 February, 2019Cybercrime: In-house protection that only YOU can provide
Cybercrime: In-house protection that only YOU can provide From the political world to the corporate, all we hear about is hacking, hacking, hacking. Every
01 February, 2019VoIP: A money saving solution for your company’s technology backbone
VoIP: A money saving solution for your company’s technology backbone When small business managers think about their IT infrastructure, they think about th
25 January, 2019SAFETY PUP SAYS Update
SAFETY PUP SAYS…. Update One thing smaller firms and individuals are often reluctant to do is download updates to their operating systems and individual
18 January, 2019With Ransomware, The ONLY Cure Is Prevention
With Ransomware, The ONLY Cure Is Prevention It just keeps showing up in the news. Ransomware seems to just not come to an end. If you haven’t heard
11 January, 2019Business Trade Shows Part II: During the Event
We’re back. In the last post, we talked about building momentum toward a trade show exhibition. Today, let’s look at your efforts during the sho
10 January, 2019Business Trade Shows Part I: Before the Event
Going to a tradeshow for the first time? Don’t make the mistake of viewing this as a 1-2 day discreet marketing event. Instead, view your exhibit at a
03 January, 2019Is Your Website Mobile Optimized?
Smaller firms often struggle just to keep up with maintaining a website. Worrying about a scaled down version for mobile users seems like just too much tro
27 December, 2018Password Basics That Are Still Ignored
You can have all the locks on your data center and have all the network security available, but nothing will keep your data safe if your employees are sloppy
20 December, 2018You’re Fired! Now Give Me Your Password
“You’re FIRED!” ( now give me your password)Losing an employee is not usually a good experience. If they leave voluntarily, you lose a valua
13 December, 2018IT Defense in Depth Part II
Defense in Depth Part IIIn our last blog we started talking about the different layers of security necessary to fully defend your data and business integrity.
06 December, 2018IT Defense In Depth Part I
In the 1930s, France built a trench network called the Maginot Line to rebuff any invasion. The philosophy was simple: if you map out all the places an ene
29 November, 2018Data Security: A People Problem
Phishing Scams – A People ProblemThere are some things that only people can fix. There are many security risks to which your data is susceptible, but there
22 November, 2018What is Ransomware and How Can it Affect Your Business?
This cyberattack scheme hasn’t garnered nearly as much attention as the usual “break-in-and-steal-data-to-sell-on-the-Internet version,” b
15 November, 2018Data Breaches are a Question of When, Not If
You hear on the news all of the time about big cyber attacks on large corporations, and even government agencies. The trouble with this news coverage is tha
08 November, 2018Penetration Testing vs Vulnerability Testing Your Business Network
Hearing “all of your confidential information is extremely vulnerable, we know this because…” is bad news, but whatever follows the ellips
01 November, 2018Benefits of Using VoIP Technology
Benefits of Using VoIP Technology More and more businesses are implementing Voice over Internet Protocol or VoIP technology because of its versatility, fl
04 October, 2018BYOD: Why is This Concept So Attractive to Employees?
BYOD: Why is This Concept So Attractive to Employees? Bring Your Own Device, or BYOD, to work was an idea a few years ago that is becoming a reality very
27 September, 2018VoIP: A New Dimension in Communication for SMBs
VoIP: A New Dimension in Communication for SMBs Voice over Internet Protocol or VoIP is about a decade old technology that is gaining popularity among ind
20 September, 2018SMBs: It is Hackers v You – Don’t Let Them Score
SMBs: It is Hackers v. You – Don’t Let Them Score Selling stolen IDs and other personal data is a lucrative trade for hackers. They are always
13 September, 2018Business Disaster: What Threatens Small Businesses the Most?
Business Disaster: What Threatens Small Businesses the Most? There are many threats to the integrity of a small business, and not all of them are as dramat
06 September, 2018Data Protection and Bring Your Own Device to Work
Data Protection and Bring Your Own Device to Work BYOD refers to a firm’s policy of allowing employees to use their own personal phones, tablets and
30 August, 2018Everyday Human Error Can Affect Data Protection
Everyday Human Error Can Affect Data Protection Are you under the impression that data loss is all about putting up firewalls to protect against evil cybe
23 August, 2018Disaster Recovery Plans: Do You Have One?
Disaster Recovery Plans: Do You Have One? Disaster recovery and business continuity plans are issues that almost all small businesses fail to think about. Mor
16 August, 2018Why Small Businesses Shouldn’t Avoid Making Disaster Recovery Plans
Why Small Businesses Shouldn’t Avoid Making Disaster Recovery Plans. Entrepreneurs and small businesses, especially ones that are fairly new, often
09 August, 2018Outsourcing? Really Its OK: How it can save time and money
Outsourcing? Really. Its OK: How it can save time and money Almost by definition, small business owners and entrepreneurs cringe at the concept of outsour
02 August, 2018Run your Business, not an IT Company
Run your Business, not an IT Company You went into business because you have an interest and expertise in some particular product or service. You began th
26 July, 2018What is the Cloud: A Simple Analogy
The Cloud: Are there security issues? For many, the idea of offloading their data to another physical/virtual location can seem like a security risk. It see
19 July, 2018Loss of Data: Causes and Prevention
Loss of Data: Causes and Prevention The adoption of technology from the simplest of matters to the most complex problems has rendered us heavily dependent
12 July, 2018Be Proactive: How to Avoid Potential Network Failures
Be Proactive: How to Avoid Potential Network Failures For small- to medium-sized businesses (SMBs), an IT network failure can be devastating because they
05 July, 2018It is Heaven! Using the Cloud to Challenge Big Business
It is Heaven! Using the Cloud to Challenge Big Business Has anyone suggested you begin moving your business to the cloud? Cloud data storage or cloud comp
28 June, 2018Smaller firms less likely to keep up to date on the basics that protect them
Smaller firms less likely to keep up to date on the basics that protect them. On the never ending problem of cyber security, small firms often do not have
14 May, 2018Huntington Technology, Inc. Achieves Enterprise Partner Status with Datto
FOR IMMEDIATE RELEASE: May 11, 2018 | CONTACT: Steve Krasnick, 248.357.7200 Protecting Clients’ Data from Ransomware, Theft, and Natural Disasters Southfield, M
14 May, 2018Cyberattacks and the vulnerability of the small business
Cyberattacks and the vulnerability of the small business You cannot go a day without reading about some big name company or even government agency being h
07 May, 2018Denial is not a solution: Something you owe your customers and your employees
Denial is not a solution: Something you owe your customers and your employees Why do so many people procrastinate about making a will? Why is it so hard t
30 April, 2018Limited investment capital and planning for trouble
Limited investment capital and planning for trouble Small businesses often fail to take the time to make business continuity plans. One aspect of a busine
23 April, 2018Data Protection Laws and PIIs
Data Protection Laws and PIIs Last week we discussed the overall concept of “Data Protection Laws,” which govern the handling and securing of specific data. Whi
16 April, 2018Are you subject to Data Protection laws?
Are you subject to Data Protection laws? This blog introduces a new topic that many may be unaware of: Data Protection laws. These are laws that define fu
09 April, 2018Ransomware Part II
Ransomware Part II In our last blog, we explained what ransomware is, and why it can be an especially troublesome virus. Today, let’s look at what you can
02 April, 2018Ransomware part I
Ransomware part I The daily reports of cybercrime are important reminders about the need to protect your business from malicious behavior that could threa
26 March, 2018HT Accepts Datto Hall of Fame Award
HT’s own William Bluford was at DattoCon16 this year and accepted an award on our behalf for the Datto Hall of Fame! Huntington Technology Selected for D
29 June, 2016Don’t let your IT Infrastructure Fall Behind
What does end of support for Windows 2003 mean for you? After July 14, Microsoft will no longer be issuing security updates or providing support for any versio
13 May, 2015Winter 2014 Tech Tips
Greetings and News from the team at Huntington Technology Hello HT business colleagues and friends, Best wishes to all of you for a very happy, healthy and safe
26 January, 2015Holiday Criminals
Black Friday and Cyber Monday are just around the corner, and companies will be kicking off their holiday shopping madness. It’s also a time for thieves to be
21 November, 2014Tech News and Tips – July 2014
Moving Day! Is your company growing? Have you outgrown your current office space and looking to move somewhere new? Moving into a new office can be exciting, bu
30 June, 2014Are you prepared for disaster?
Did you know that almost 90% of all email messages to our clients are SPAM? That’s what our SPAM filter statistics are averaging across all of our clients
11 June, 2014Nightmares About Data Backups?
Do you know when you should worry about backing up your files and protecting your IT infrastructure? The answer isn’t AFTER something bad happens… I
30 July, 2013First Aid for Gadgets – Whitepaper
For better or worse, we’re more reliant on our handheld gadgets than ever. So when things go wrong — e.g. your smartphone’s battery dies at the worst poss
24 July, 2013Tech News and Tips – June 2013
Monthly tech news + tips from Huntington Technology, Inc. Does your business have a cybersecurity plan? In 2012, companies with just one to 250 employees
01 June, 2013Tech News and Tips – May 2013
Monthly tech news + tips from Huntington Technology, Inc. Turn your small business into a tech powerhouse Ensure your business possesses the right techno
01 May, 2013VoIP at a glance – Whitepaper
Every business wants to cut costs, right? In our continued economic slump, we’ve found that many businesses have an added extra urgency in this regard—which exp
27 April, 2013Tech News and Tips – April 2013
Monthly tech news + tips from Huntington Technology, Inc. Email Etiquette for a Busy World How to be a graceful and effective communicator in the digital
24 April, 2013Tech News and Tips – March 2013
Monthly tech news + tips from Huntington Technology, Inc. Soaked Gadgets: How You Can Save Them Accidents happen. Here’s what to do when they involve liqu
04 March, 2013Tech News and Tips – February 2013
Monthly tech news + tips from Huntington Technology, Inc. Square and Your Business: Match Made in Heaven? Should businesses cheer the arrival of Square?
24 February, 2013Your guide to Telecommuting Security – Whitepaper
With a couple of recent studies showing that telecommuting can actually *improve* worker productivity and morale, we expect that more local businesses will let
24 January, 2013

































































































![Enterprise_Partner_Logo_[JPEG]](https://huntingtontechnology.com/wp-content/uploads/2018/05/Enterprise_Partner_Logo_JPEG.jpg)